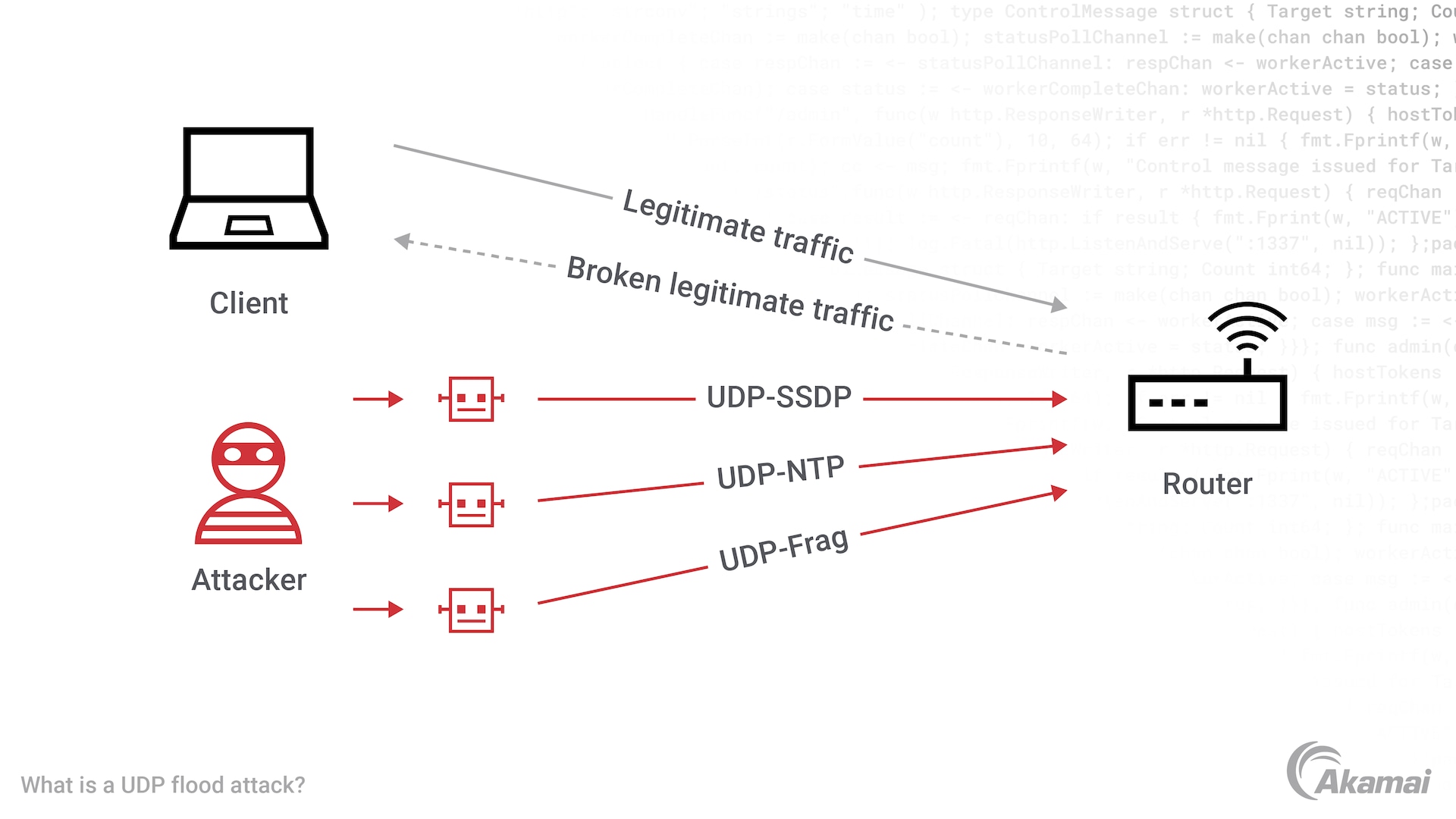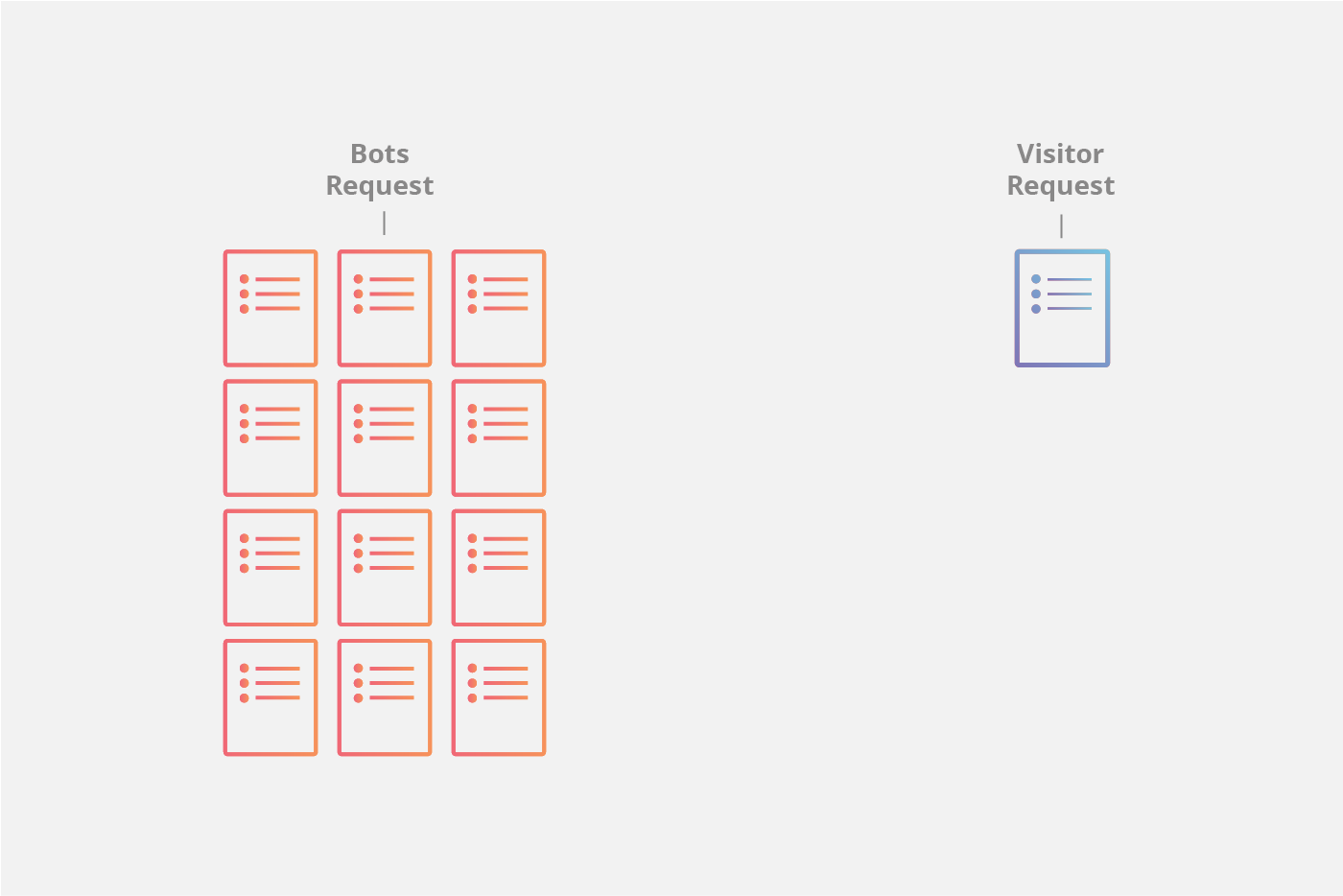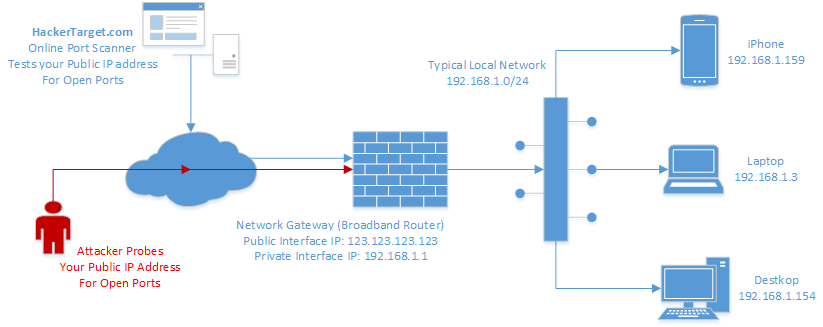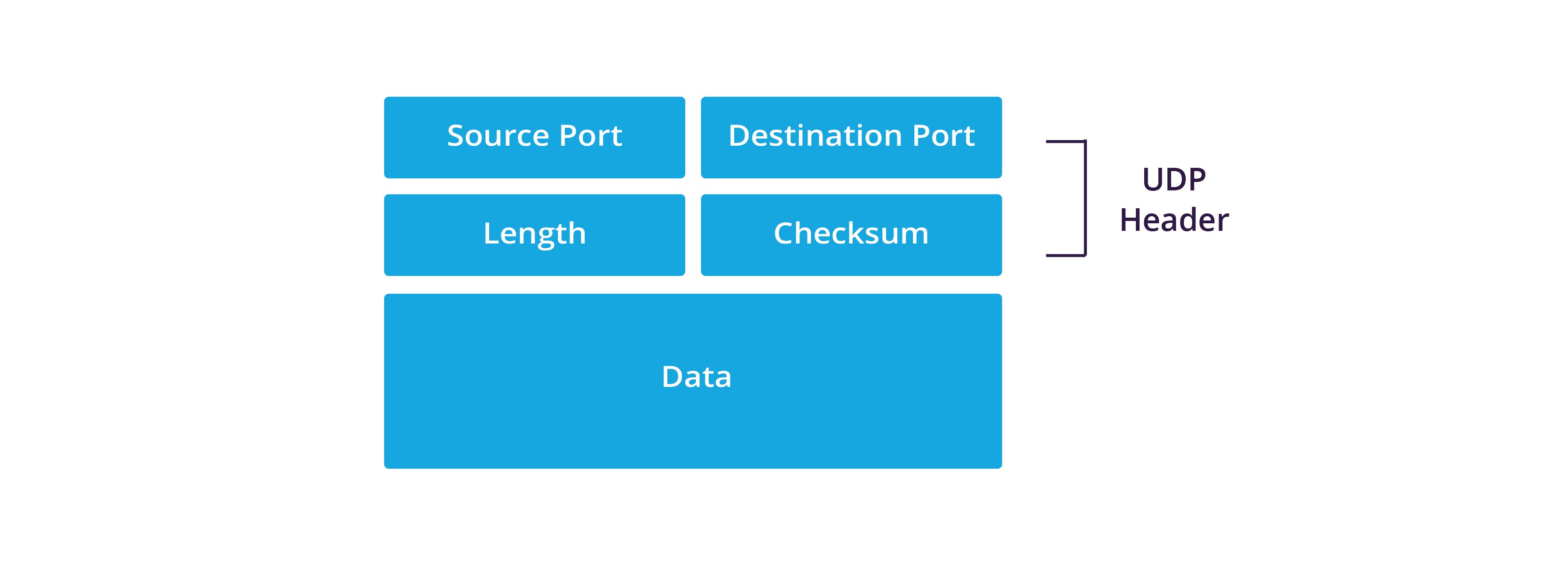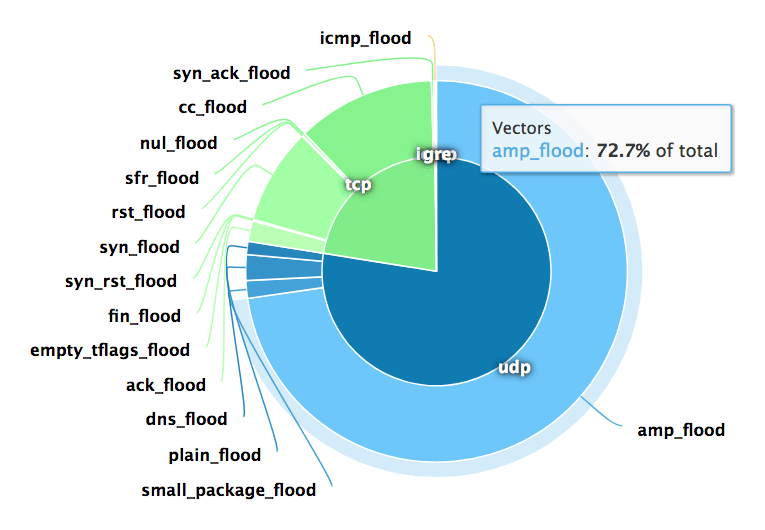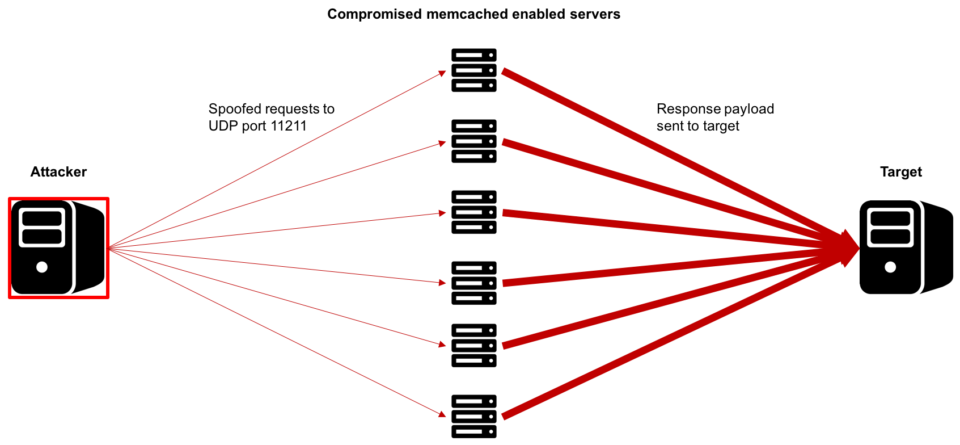
Use Dome9 to Prevent Memcached-based DDoS Attacks from Your Cloud Environment - Check Point Software

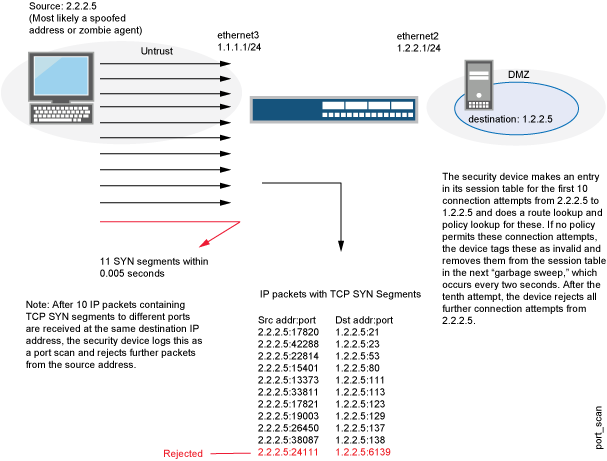
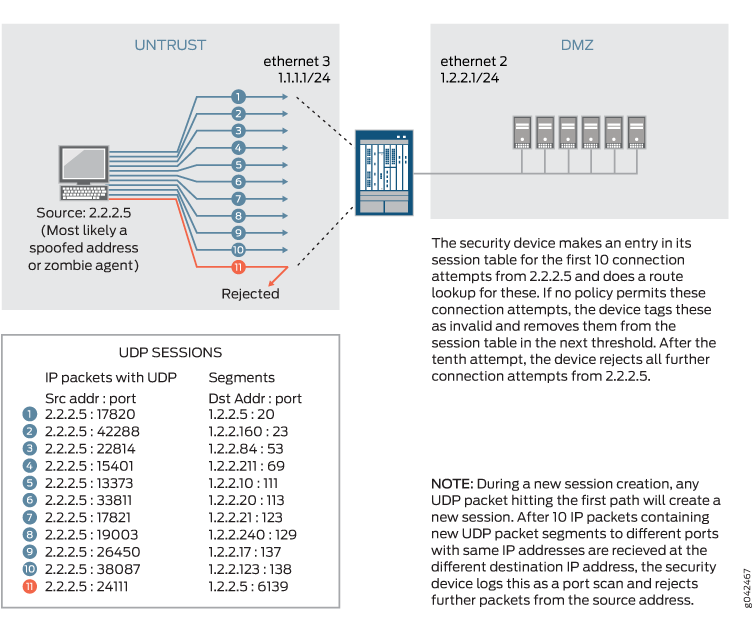
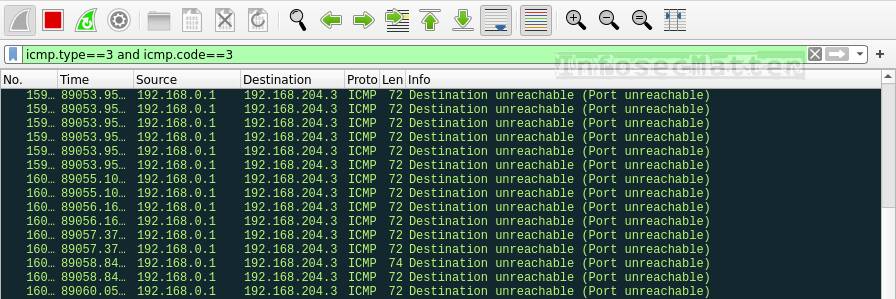
Connections Attempts (a) normal TCP connection (b) TCP port closed (c)... | Download Scientific Diagram

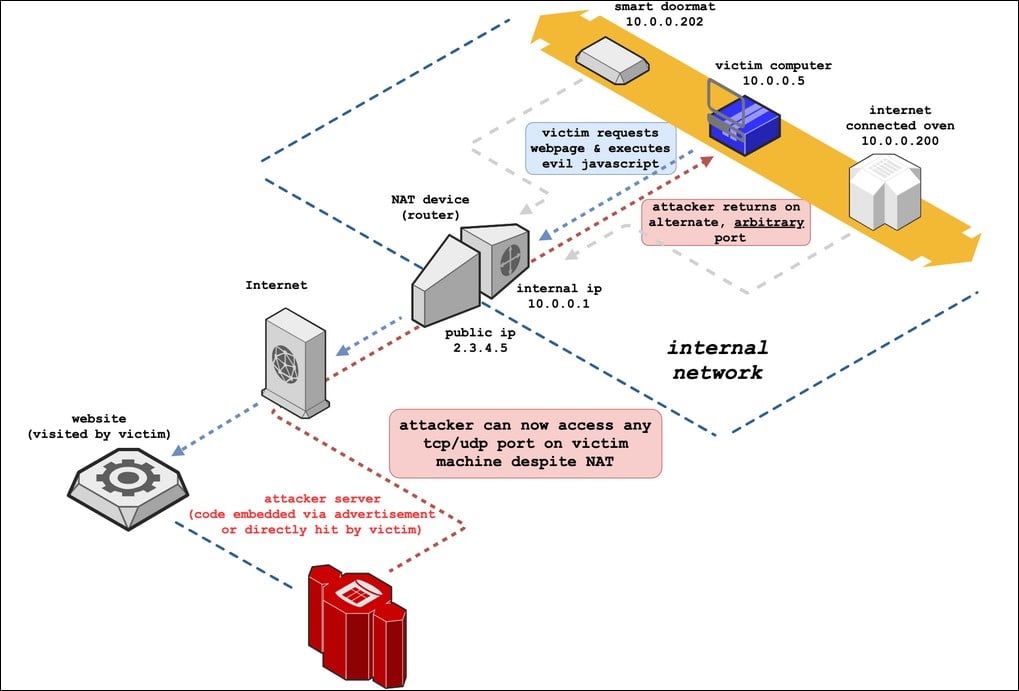
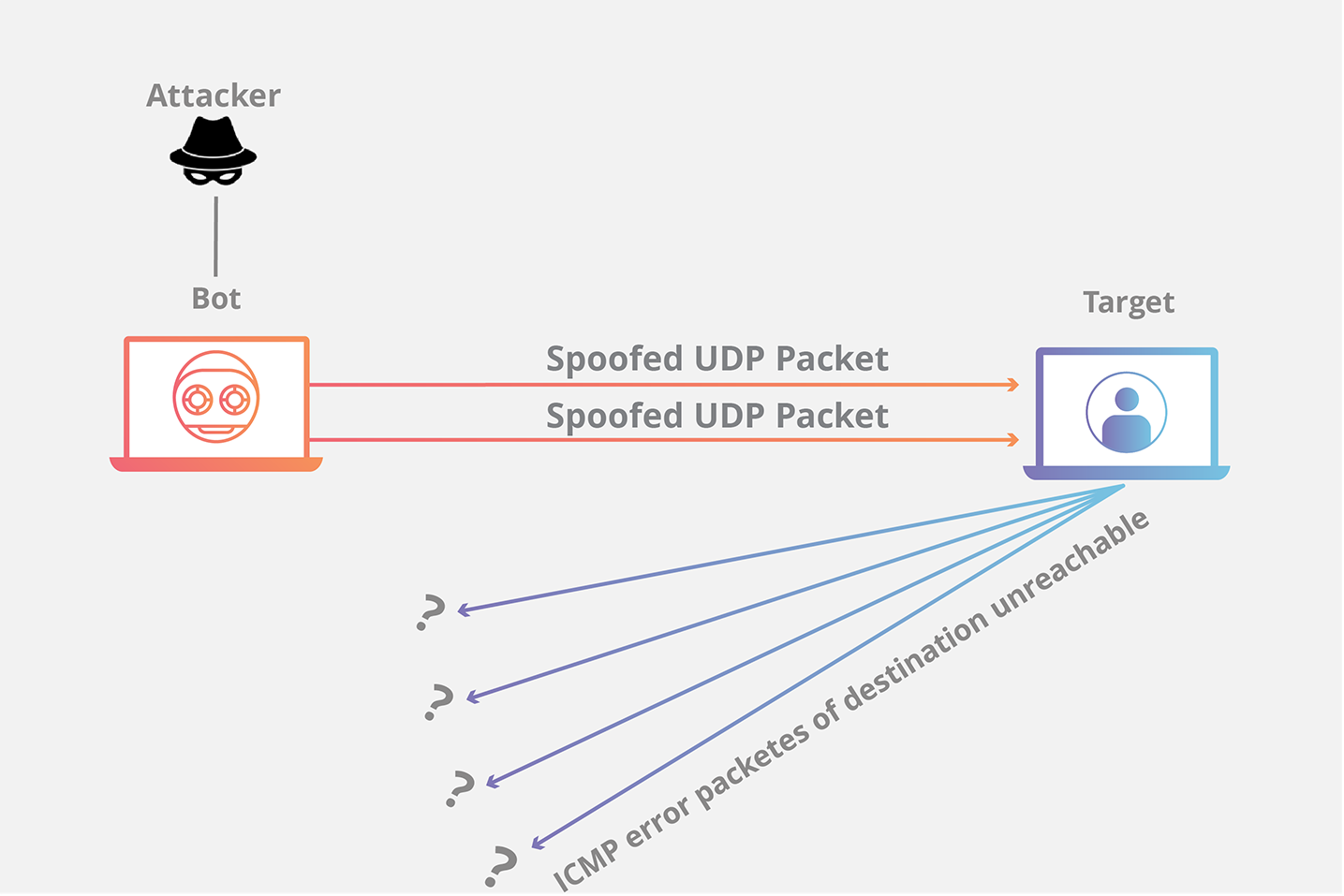
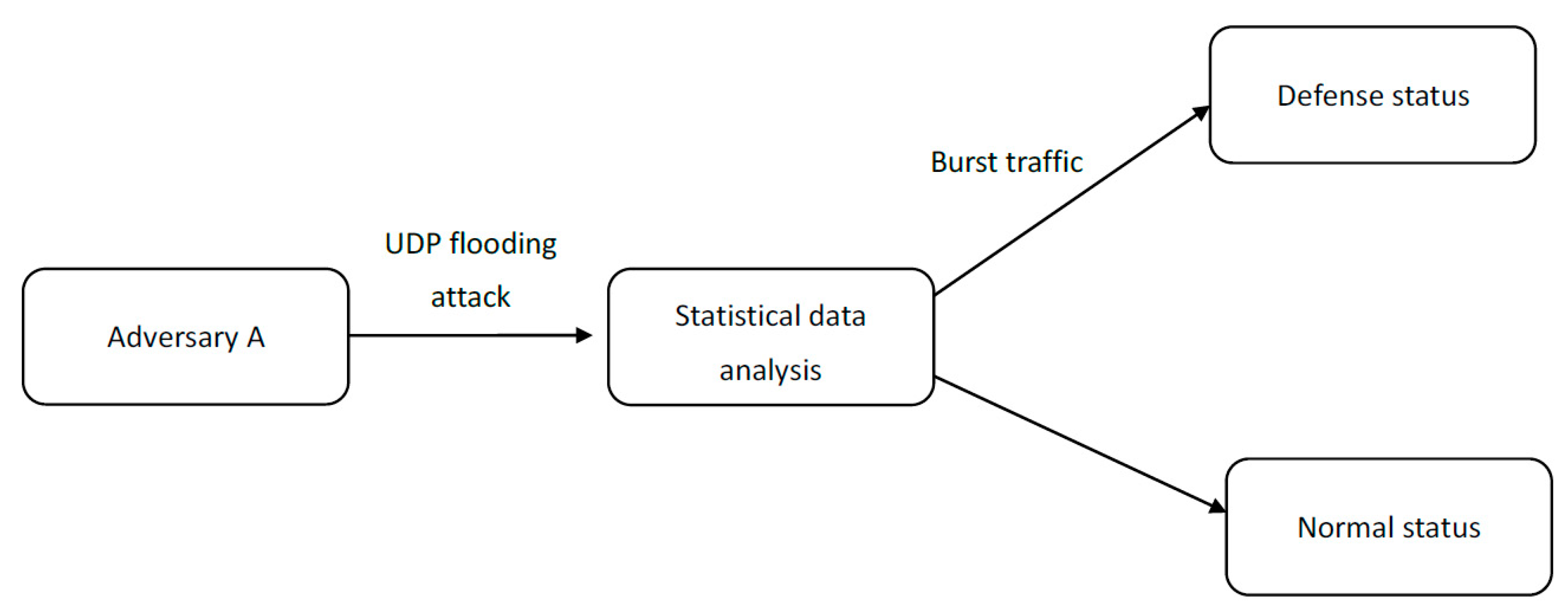
UDP Flood attack not interrupted and the two communicating hosts' will... | Download Scientific Diagram